Diagnostics & Troubleshooting
Detect Pegasus and Other Spyware on iPhone and iPad

💡iMazing 3
This guide is not yet complete or updated for iMazing 3. An update will be available soon.
iMazing's spyware detection tool is available as a free feature in iMazing 2.14 and above. It can be used to detect signs of infection by NSO's Pegasus and has the potential to evolve to detect other threats. The methodology implemented closely mirrors that of the open-source Mobile Verification Kit by Amnesty International's Security Lab. The ability for the user to customize the analyzer by providing indicators of compromise in STIX format may be useful for early investigations of future threats. For more context on the development of iMazing's spyware detection tool, please refer to this blog post.
⚠ Important disclaimer: iMazing cannot prevent spyware infection. It can only detect signs of current or past infections by looking for known malicious file names, links, process names and emails. A clean scan does not guarantee that your device is not infected. Results may be difficult to interpret and may contain false positives.
Please read the documentation carefully before proceeding. It is especially important for high risk individuals to understand the scope and limitations of iMazing's spyware analyzer so as not to develop a false sense of security – see 1.3 Scope and Limitations below. This tool does not replace expert assistance.
Here's how to detect Pegasus and other spyware using iMazing's spyware detection tool:
- Launch iMazing on your Mac or PC and connect your iPhone or iPad via USB.
- Unlock your device and enter your passcode to establish pairing with the computer.
- In the Actions panel, scroll down and click Detect Spyware.
- Follow the information and configuration steps carefully.
- Read the analysis report and refer to the documentation for help.
Documentation
1. Before you begin
1.1 Our commitment: 100% free and anonymous
You do not need to purchase a license before using the spyware detection tool. It is available without restriction when using iMazing in trial mode – there is no registration required, and no time limit to the trial.
1.2 Privacy and internet connectivity
The spyware analyzer will look for signs of infection in a backup of your iPhone or iPad. Both the backup process and the analysis of backup files happen locally only, on your computer - strictly none of your personal data is uploaded to our (or any third party's) servers. iMazing will encourage you to enable backup encryption, which will further protect your personal data.
iMazing's spyware analyzer requires an internet connection in order to:
- Download the latest IOCs (Indicators of Compromise)
- Expand shortened links such as this link to Amnesty International's MVT project
You can learn more about iMazing's security and privacy commitments here: Security & Privacy
1.3 Scope and limitations
Just like the Amnesty International MVT tool it is based on, iMazing's spyware detection tool works by analyzing a backup of your iPhone or iPad to spot traces left by known spyware. Successful detection largely depends on finding references to known malicious links, email addresses, process names and file names compiled by the security community in STIX format. At this time, iMazing will by default download and use the latest version of the following STIX files:
- Pegasus (NSO):
pegasus.stix2from https://github.com/AmnestyTech/investigations/blob/master/2021-07-18_nso/ - Predator (Cytrox):
cytrox.stix2from https://github.com/AmnestyTech/investigations/blob/master/2021-12-16_cytrox/
As new relevant STIX files become available, they can be quickly added to iMazing's default indicators of compromise without having to update the app. If you spot a new and relevant STIX file that isn't listed here, please inform us.
Successful detection of more subtle infection patterns depends on logic that is contained in iMazing's code. It is therefore important to make sure that iMazing is fully up to date before running a spyware check.
1.4 License: consensual use only
iMazing's spyware detection tool is released under the same license as Amnesty International's MVT, an adaptation of Mozilla Public License v2.0. This modified license includes a new clause 3.0, "Consensual Use Restriction", which permits the use of the licensed software exclusively with the explicit consent of the person/s whose data is being extracted and/or analysed ("Data Owner").
2. In depth tutorial
2.1 Install or update iMazing
Make sure that you have the latest iMazing version installed on your computer before running a spyware check. You can check for updates within iMazing, or download and install the latest update here:
Download and install iMazing on your Mac or PC computer.
2.2 Connect your device and launch the analyzer
After launching iMazing, you can connect your iPhone or iPad to your computer, or analyze an existing backup. In both cases, you only need to select your device (or device backup) in iMazing's left sidebar and click Detect Spyware to get started:
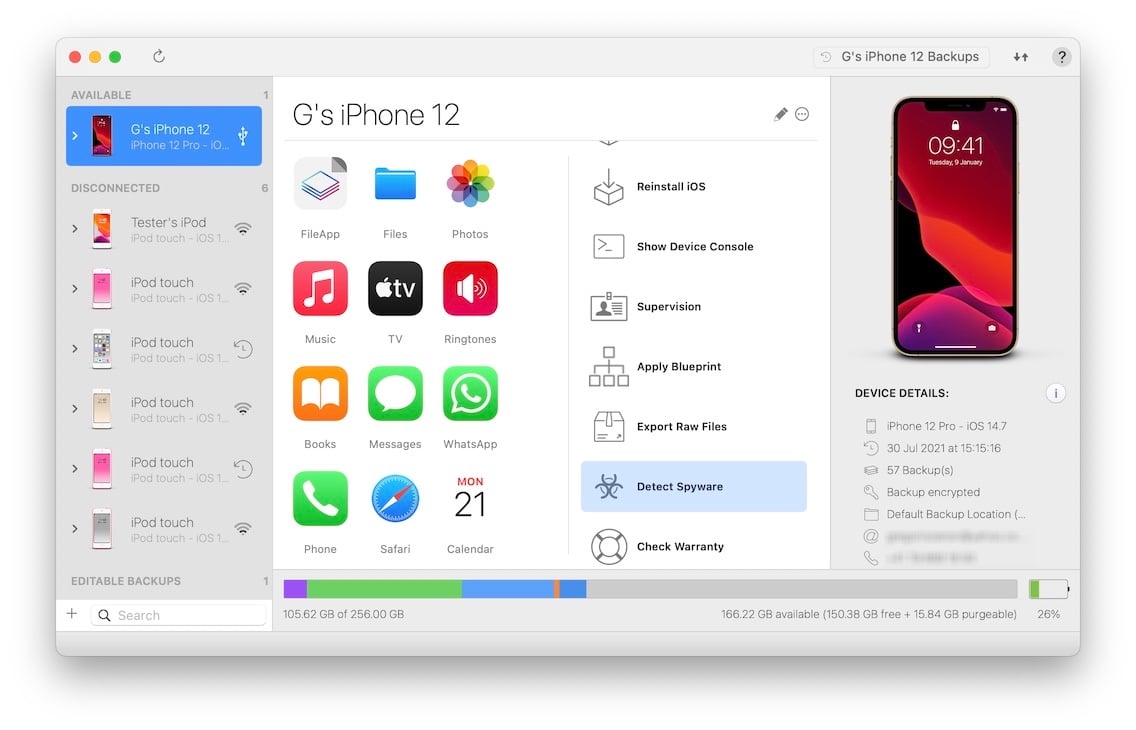
Note that you may need to scroll down the Actions panel to locate the Detect Spyware action.
💡 Security tip: if it is your first time connecting your mobile device to your computer, iMazing will display a pairing screen. Pairing is an Apple feature which establishes a secure link between your iOS device and your computer. Pairing requires you to enter your passcode on your mobile device. You can revoke pairing after the scan by using the Forget action of the same Actions panel in iMazing.
iMazing should now display the Detect Spyware wizard's presentation step:
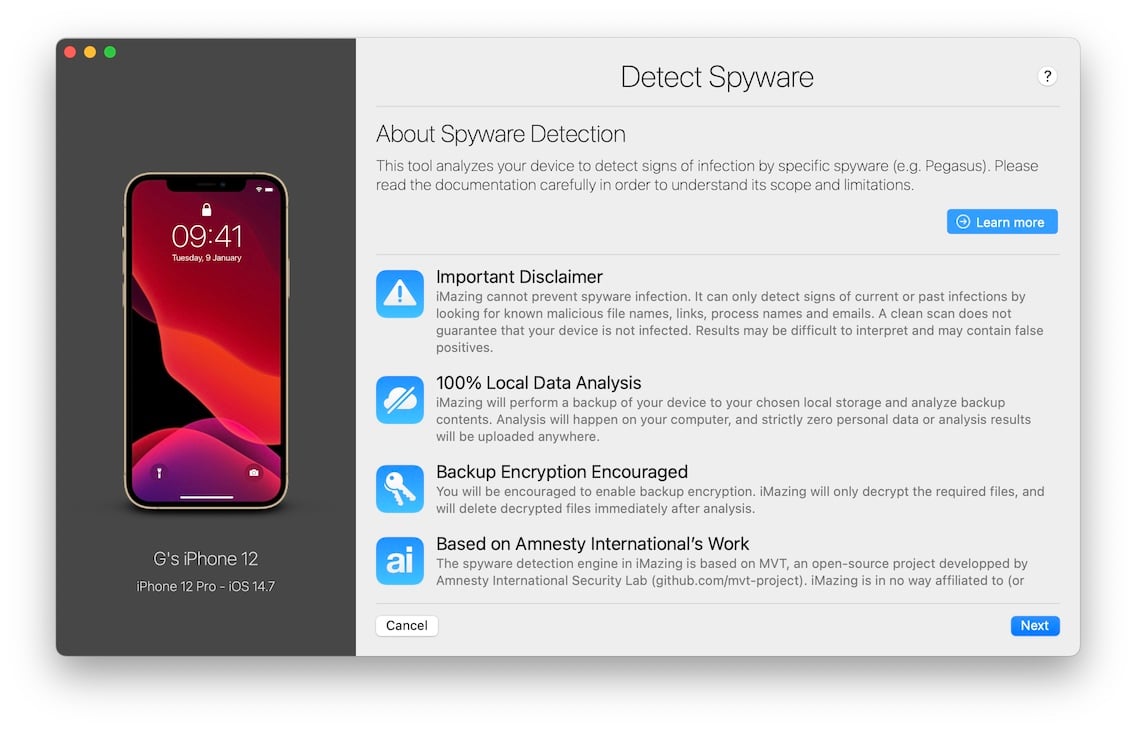
Click Next to continue to the configuration step.
2.3 Configure the analyzer
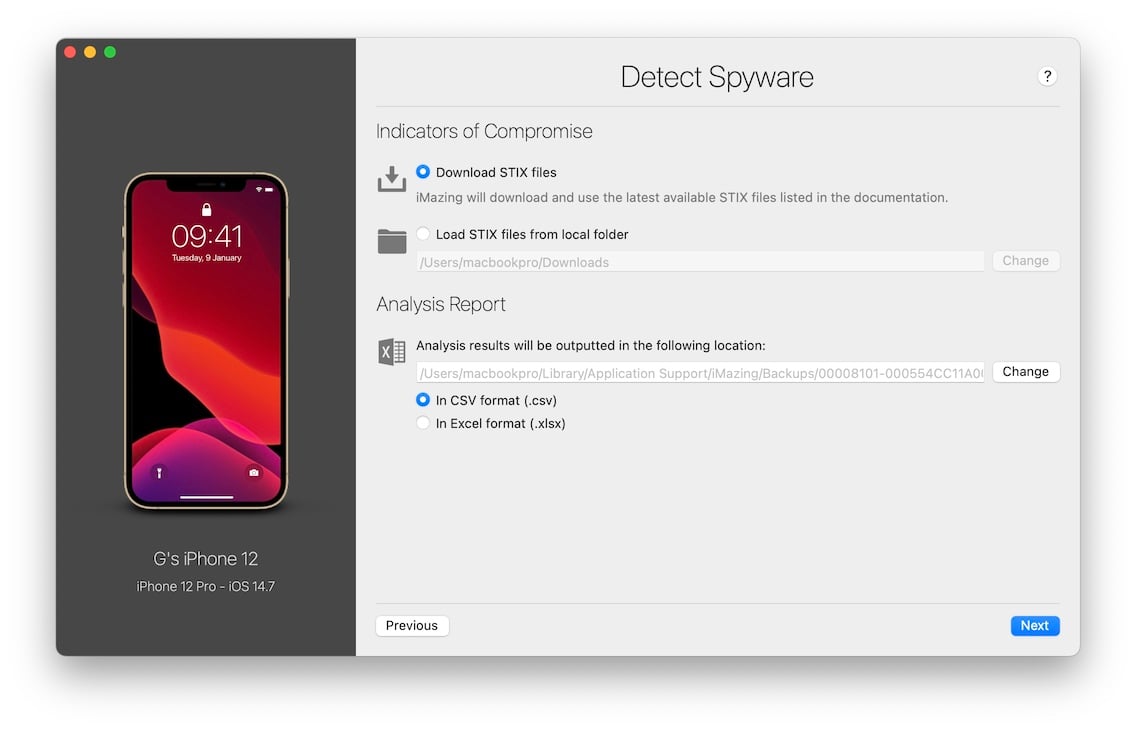
In this step, you can customize the behaviour of the analyzer. For a standard scan, you can leave the default options as they are and click Next. More advanced users can provide custom STIX files and choose the location and format of the analysis report.
Indicators of Compromise
By default, iMazing will download a list of known malicious email addresses, links, process names and file names from publicly available STIX files. You can provide your own STIX files for research purposes by selecting Load STIX files from local folder and picking a folder containing at least 1 .stix or .stix2 files.
Analysis Report
By default, the report is saved in the same folder as the device's backup, in CSV format. You can choose a different location, and opt for the Excel (.xlsx) format instead if you wish.
2.4 Review backup options
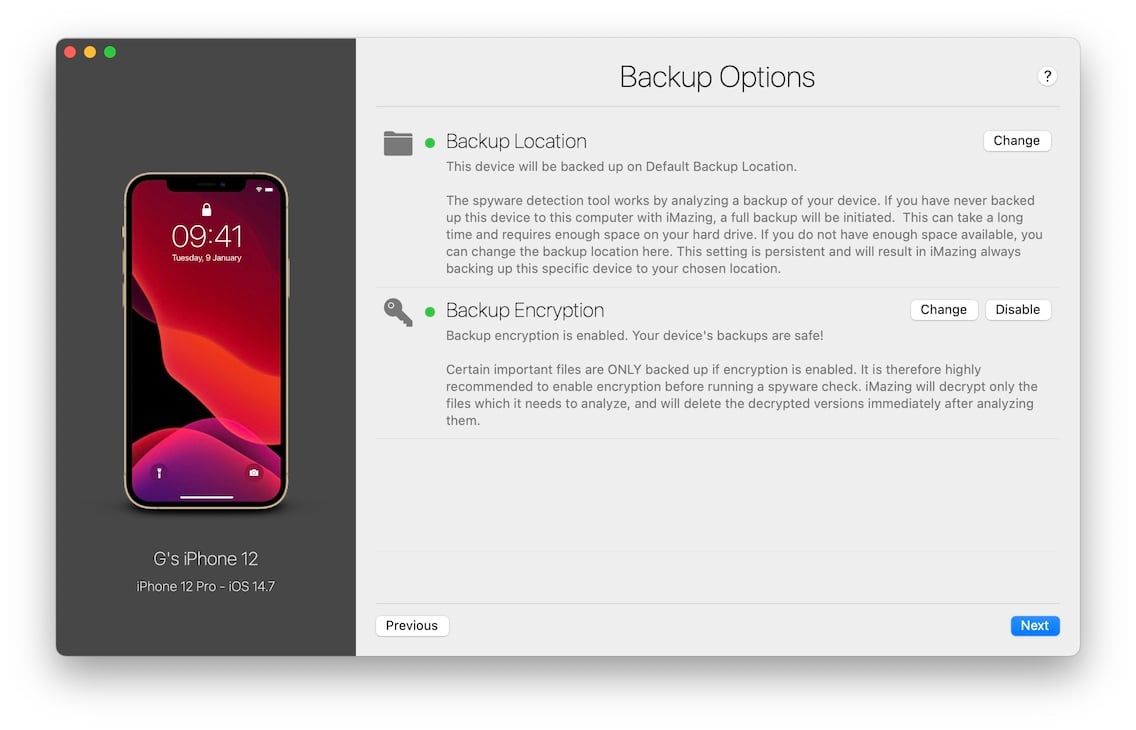
This step is only shown when analyzing a live connected device. It gives you the opportunity to change the backup location and enable encryption of all future local backups of the device, regardless of the software which performs the backup.
2.5 Accept the disclaimer and start the scan
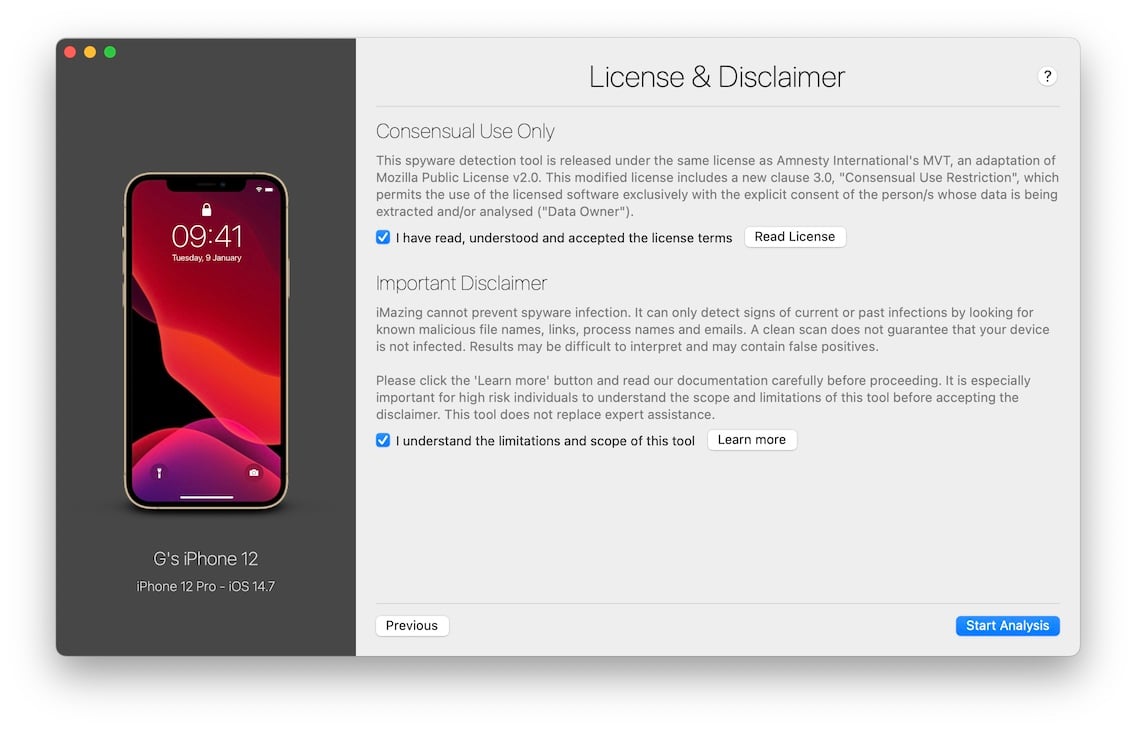
The last step before starting the scan requires you to accept a separate license. Because iMazing's spyware analyzer is based on open-source code, it's use is subject to a separate license. The disclaimer's Learn More button will take you to this article's Scope and limitations section, which you must read and understand before proceeding.
Once you have accepted both the license and disclaimer, click Start Analysis. iMazing will perform a backup of your device if needed, and will analyze files of interest. If this is the first backup of that device to your computer, please be patient as the process can take up to an hour depending on how much data you have. If you already are backing up with iMazing, an incremental backup will take just a few minutes.
During the entire process, iMazing will inform you of the analyzer's activity, from the initial backup to the download of indicators of compromise:
3. Interpreting results
Once analysis of your device's backup is complete, iMazing will display a dialog window containing a short summary of the analysis report. From the dialog window, you can open the report or reveal it's location in the Finder or Windows File Explorer.
3.1 Clean scan
This is what the dialog looks like after a clean scan:
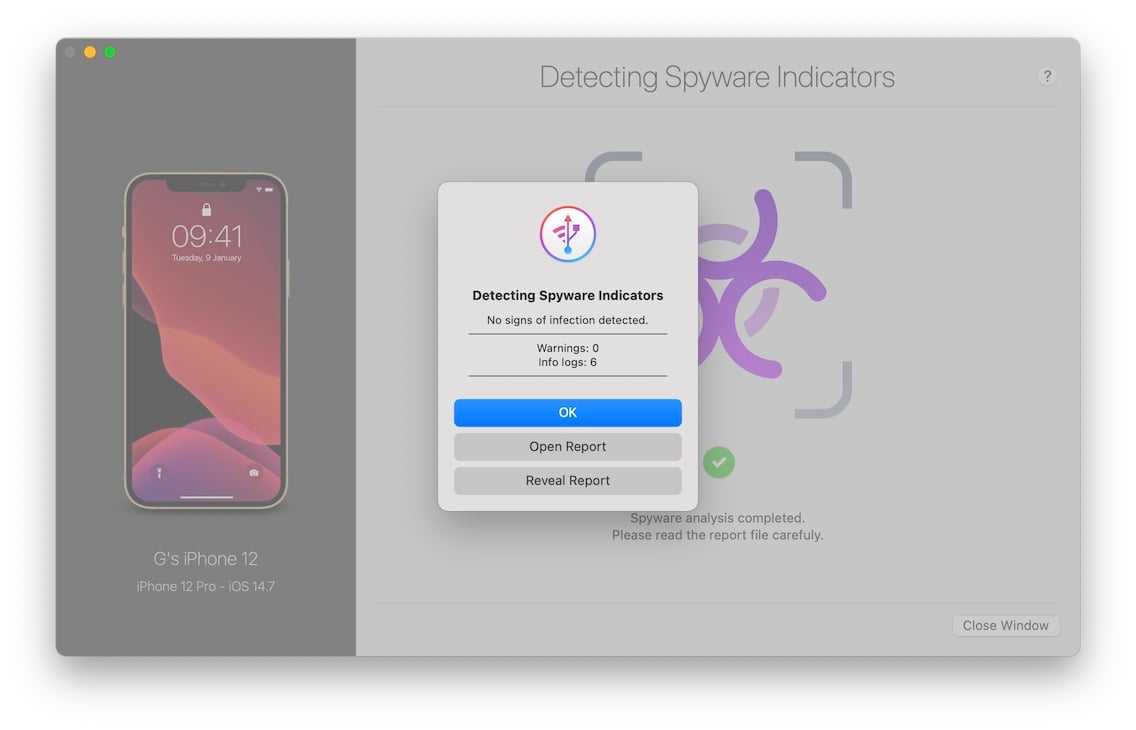
Click Open Report to open the CSV or Excel report file and review the analysis results for anything out of the ordinary. A clean report only means that no traces of spyware known to iMazing was detected, and in no way guarantees that the device is not infected.
3.2 Positive detection
This is what the dialog looks like after iMazing has detected signs of spyware activity:
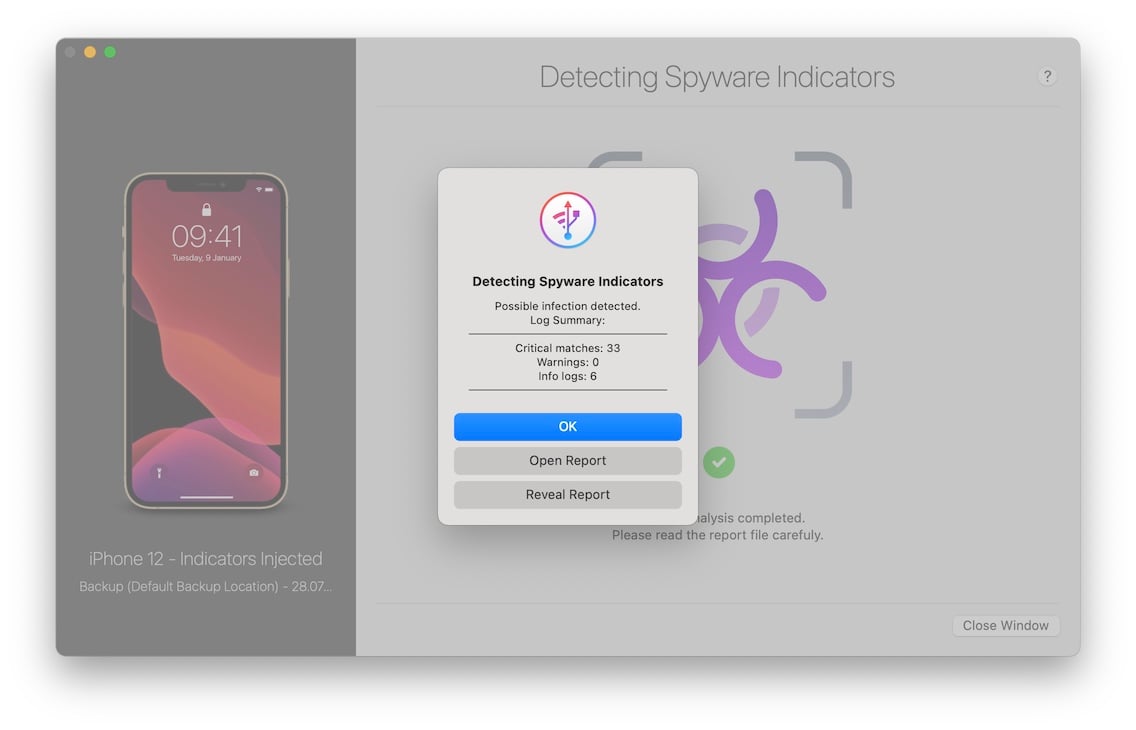
If you get a positive scan, please send us the analysis report at https://imazing.com/contact – we will check it for false positives and get back to you quickly. In the meantime, you should refrain from any communications which may put you at risk but keep using the device as you did before so as not to reveal that you have become aware of the infection. We will get back to you quickly and if needed put you in touch with professional help.
3.3 Interpreting the report
The analysis report logs information about the analysis process and eventual matches.
| Column | Description |
|---|---|
| Type | Event type, Device or Analyzer |
| Severity | Info, Warning, Critical |
| Time | The UTC time at which the event happened |
| Event | The name of the event. Indicator match, HTTP redirect, STIX download... |
| Malware | The name of the detected malware |
| Analyzer Module | The analyzer module which logged the event |
| Analyzer Time | UTC time when the event was logged |
| Description | A human readable description of the event |
The first column (Type) lets you quickly identify events which relate to the analysis itself (Analyzer events) and events which happened on the device itself and get picked up by the analyzer (Device events).
Analyzer events
The report logs the analyzer's work: downloading the STIX file, backing up the device, extracting and analyzing data from various databases... getting warnings in this type of event does not indicate infection, but brings your attention to the fact that the analyzer couldn't perform a specific task, such as extracting a file or expanding a URL.
Device events
Suspicious patterns and straight out matches are logged as Device events: HTTP redirections, indicator matches, and signs of manipulated entries will end up here. HTTP redirects are logged as warnings to bring your attention to them, they are not a sign of infection in themselves as long as they do not point to a known malicious domain.

