Detecting Pegasus Spyware with iMazing

At a glance
- Revelations of widespread use of the Pegasus spyware by authoritarian governments have recently shocked the world.
- In this context, Amnesty International published MVT, an open-source command-line tool designed to help investigators and technologists detect signs of infection in mobile devices.
- We have implemented MVT's detection methodology as an easy to use and entirely free feature in iMazing.
- No fear-mongering here – the vast majority of iPhone users aren't at risk. Our hope is that by lowering the technical barrier of entry, we may raise awareness and facilitate early detection of threats.
- The spyware detection feature was crafted with great care to ensure that its users are adequately informed of the scope and limitations of the procedure.
- Getting started only requires the anonymous download and installation of iMazing 2.14 on a PC or Mac. The feature is fully available without purchasing a license. Detailed instructions can be found here.
The Pegasus Project
Apple mobile devices and the iPhone in particular are generally regarded as highly secure consumer-grade computing devices. Apple's commitment to security is very real, and that commitment is made evident by the very design of iOS as well as by a steady flow of new features aiming at enhancing user privacy and security. Yet, in July 2021, The Pegasus Project revealed widespread use of military-grade spyware by repressive governments targeting both Android and Apple phones.
These revelations highlight anti-democratic use of advanced surveillance technology which goes far beyond the scope of legitimate criminal or terrorism investigations. Particularly disheartening is the fact that no iPhone is safe – even the latest and fully updated devices were targeted, and successful infections have taken place without any user interaction ('zero-click' attacks). In some cases, all it took was to receive a malicious message, which could then be deleted by the attacker before the user ever became aware of the attack.
Amnesty International's Mobile Verification Toolkit (MVT)
In order to prove widespread and overreaching use of surveillance, The Pegasus Project needed to perform digital forensics on the devices of multiple targeted politicians, activists, journalists and lawyers. In that context, Amnesty International's Security Lab developed generic mobile spyware detection methodology and compiled a list of IOCs (Indicators of Compromise) related to Pegasus infection. From Amnesty International's Pegasus Forensic Methodology Report:
In this Forensic Methodology Report, Amnesty International is sharing its methodology and publishing an open-source mobile forensics tool and detailed technical indicators, in order to assist information security researchers and civil society with detecting and responding to these serious threats._Source: _Forensic Methodology Report: How to catch NSO Group’s Pegasus
The open-source mobile forensics tool mentioned above is the Mobile Verification Toolkit (MVT). According to the project's README file, MVT's goal is to "simplify and automate the process of gathering forensic traces helpful to identify a potential compromise of Android and iOS devices".
Spyware detection in iMazing
After studying the Mobile Verification Toolkit's Python code, my colleagues and I quickly realized how uniquely positioned we were to facilitate the process even further. iMazing is built on a toolkit which was developed and refined over a decade for the purpose of simplifying iOS backups, file transfers and local device management tasks. It would therefore be possible to relatively quickly re-implement MVT's methodology in our toolkit, and integrate a user-friendly 'wizard' in iMazing's user interface. And because iMazing can already perform iOS backups and decrypt backup files, the tool we envisaged had the potential to dramatically reduce the technical barrier of entry whilst enhancing performance and promoting backup encryption.
At the same time, we started getting Pegasus-related requests from current iMazing users, and noticed increasing interest in MVT from a public not always tech-savvy enough to successfully run its command-line tools. We took the plunge, shifting most of our Windows and macOS development resources to the realisation of a fully integrated equivalent in iMazing. Today, we are releasing the result of that work as a free feature in iMazing 2.14. No setup or prior backup is required – all it takes to get started is to launch iMazing, connect an iPhone and select the Detect Spyware action:
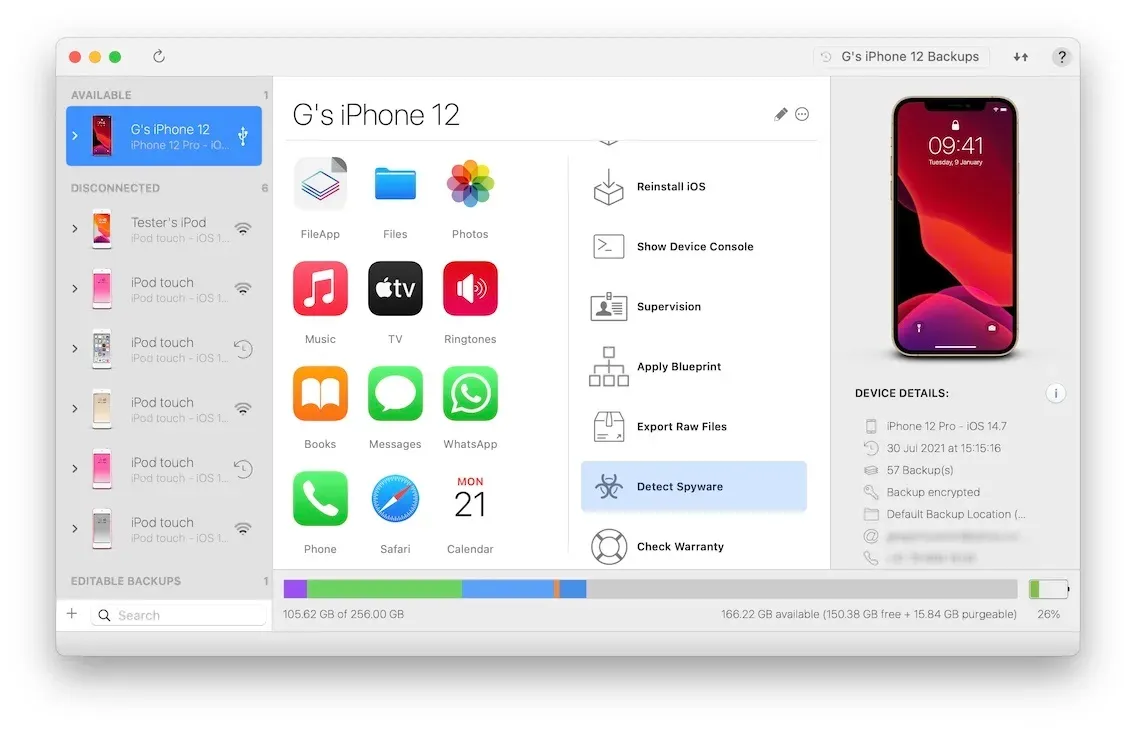
Differences and similarities with MVT
Our spyware analyzer mirrors MVT's methodology very closely:
- The same backup files are analyzed, with a few additions.
- Records are matched against the same known malicious email addresses, links, file names and process names (Indicators of Compromise).
- The same custom logic is implemented to detect foul play which can't be spotted by matching IOCs.
In addition, it offers the following enhancements:
- Zero configuration required.
- Integrated backup of the analyzed device.
- Backup encryption encouraged, and proposed before analysis.
- Working with encrypted backups does not require decryption of all backup files. iMazing decrypts only the files needed by the analyzer, and deletes the decrypted copies immediately after analysis. This results in substantial disk usage, speed and privacy improvements.
- Configuration UI allows for custom STIX files and choice of the analysis report format (CSV and Excel).
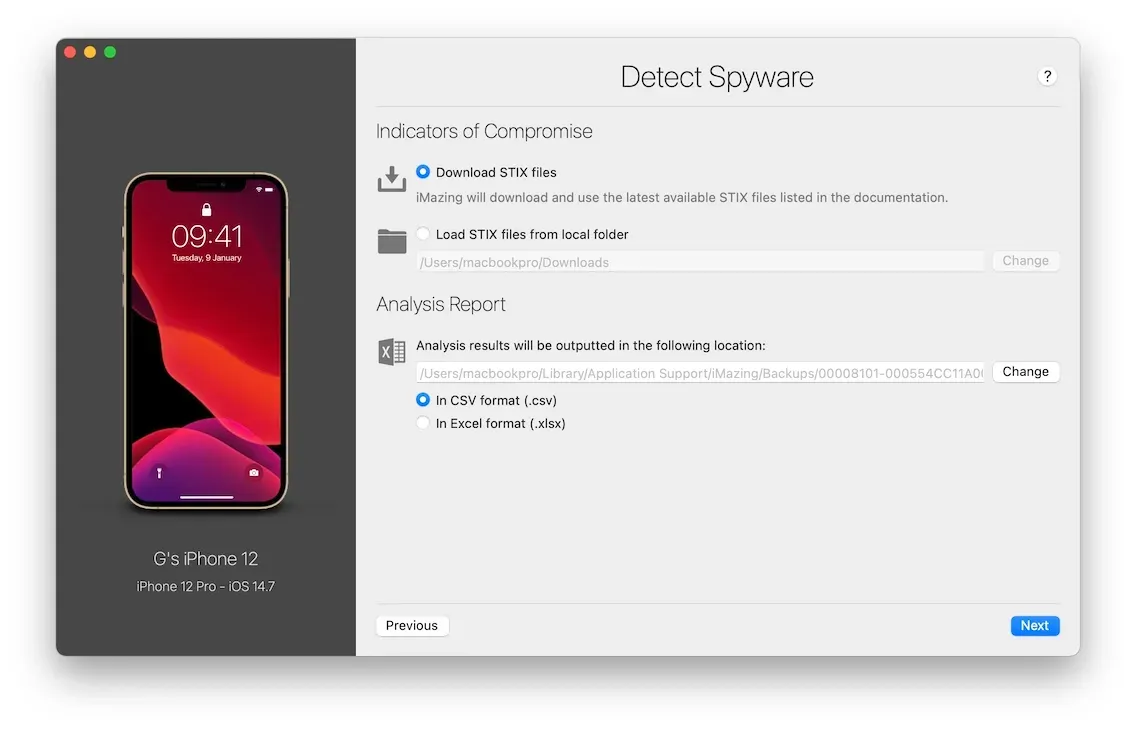
But also the following downsides and voluntary omissions:
- No support for Android, iOS only.
- No support for analyzing file system dumps from jailbroken devices.
- Extracted records are not saved to file, they are analyzed in memory before being discarded. The output therefore only contains analysis results and not the analyzed data itself.
- The open-source code of our analyzer is dependent on iMazing's proprietary toolkit. In consequence, it cannot be built as a standalone tool.
Scope and Limitations
iMazing's spyware analyzer is limited to the detection of a subset of known threats. It does not prevent infection. Its results may be hard to interpret and do not replace expert advice. Its ease of use and low barrier of entry is not without risks, in that some among its users could develop a false sense of security.
For all the reasons listed above, we have taken great care to include upfront information relative to the scope and limitations of our tool every step of the way, translated in all of the eleven languages iMazing supports. Here is the final screen of the wizard:
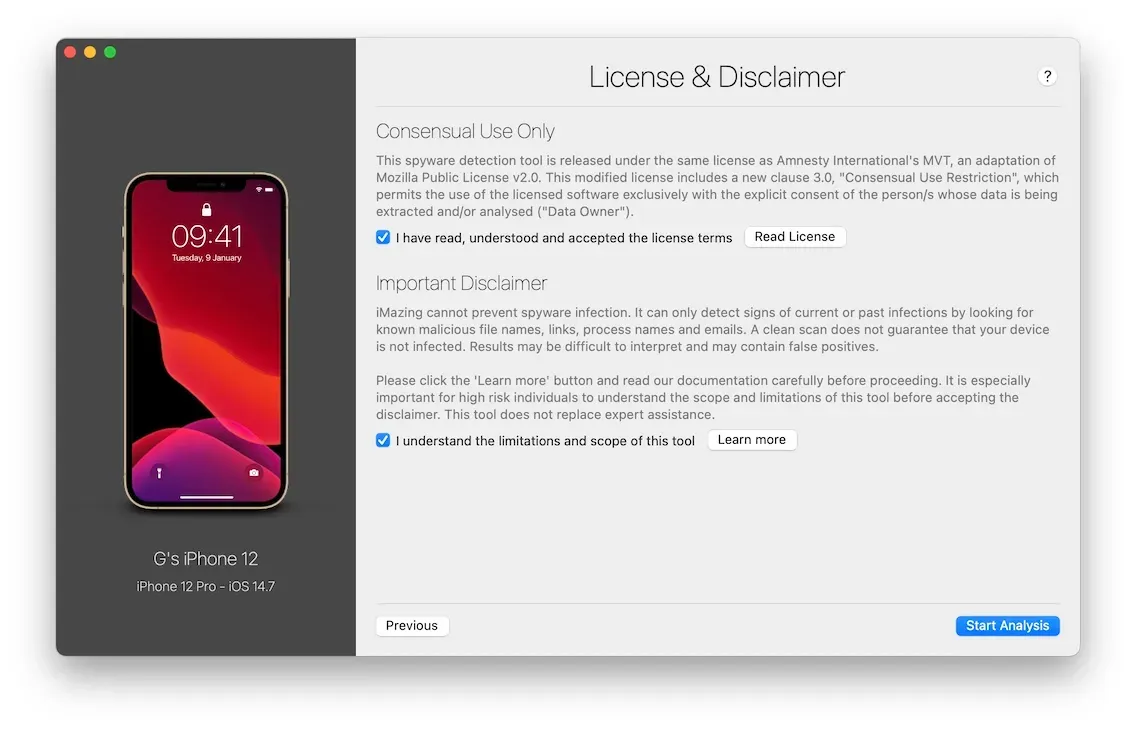
Final words: no fear-mongering, but vigilance and gratitude
The vast majority of iPhone users have never been targeted by spyware such as Pegasus. Yet, we cannot be blind to the fact that military-grade spyware is being deployed in shockingly petty and corrupt contexts by governments which we don't typically associate with liberticide authoritarian regimes. This attack targeting a prominent health official and two NGO directors in Mexico comes to mind – the victims were citizens of a republican democracy who defended a soda tax project, not political dissidents in a dictatorship.
We all feel revolted and compelled to act when human rights come under attack in such dystopian ways. NGOs, journalists and citizens of all nationalities already work tirelessly to protect our freedom, sometimes at the risk of their lives. They deserve our gratitude and support.
Gregorio Zanon
Links
- Amnesty International - The Pegasus Project
- Amnesty International - Pegasus Forensic Methodology Report
- Amnesty International - Pegasus Indicator of Compromise
- Amnesty International Security Lab – Mobile Verification Toolkit (Github)
- iMazing Malware Analyzer - C++ codebase derived from MVT (Github)
- iMazing spyware detection tool - Documentation
- The Citizen Lab - Mexico's 'Bittersweet' report