Apple increases pairing security in iOS 11, Face ID likely factor
At a glance
- Pairing between an iOS device and a computer is a security feature which guarantees that only trusted computers can access data from a particular device.
- Pairing can be misused to facilitate data theft, surveillance, investigative overreach and domestic snooping.
- In iOS 11, pairing is protected by an extra layer of authentication which largely prevents such misuses.
- The iPhone 8's much rumored Face ID authentication may have played a part in this move.
We recently became aware of a new security feature in iOS 11 which makes it much harder for ill-intended attackers or snoops to access user data stored on iPhone or iPad from a computer.
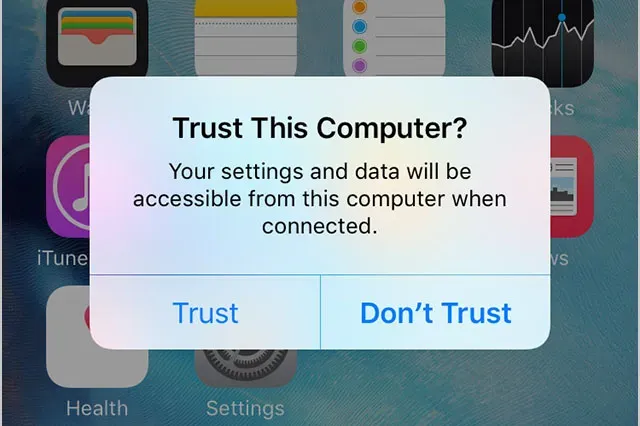
In effect, pairing an iOS device with a Mac or PC computer will not only require the iOS device to be unlocked, but will now also request passcode authentication after the Trust This Computer prompt on the device:
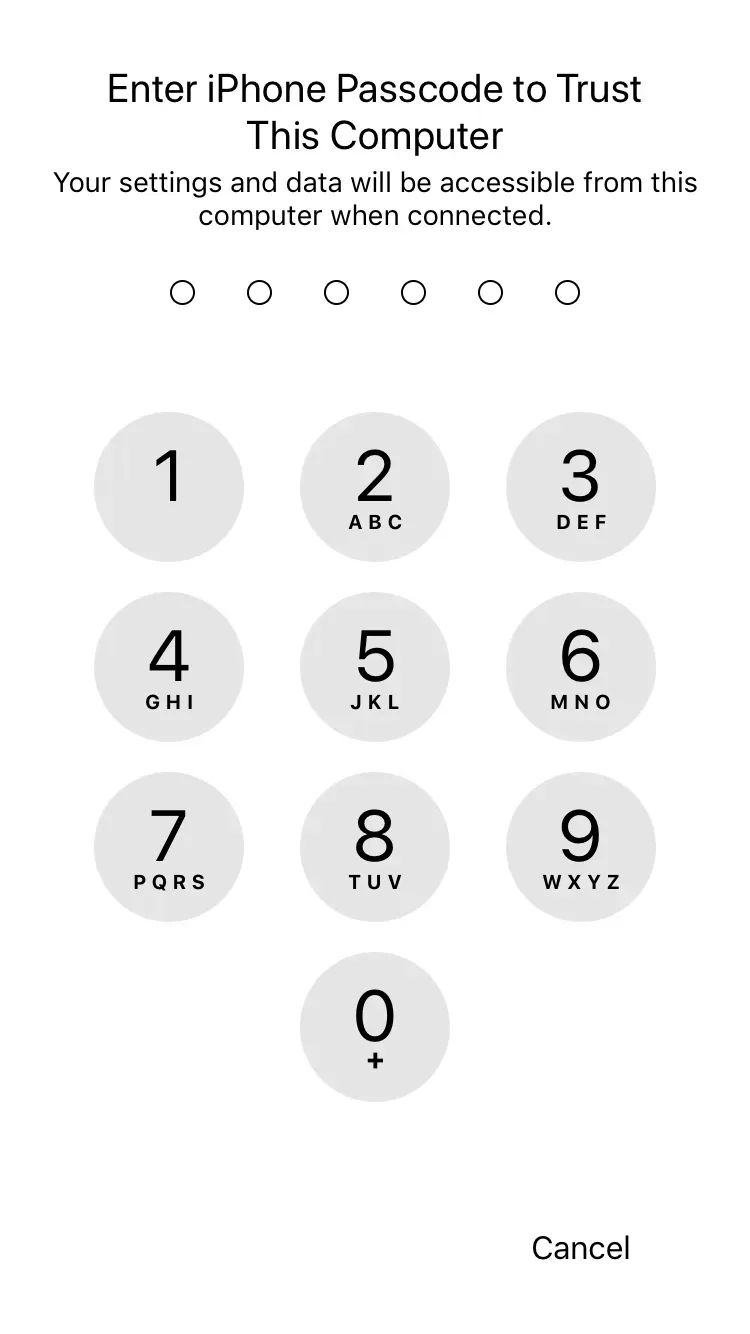
This new security feature was first reported by Redmond Pie when iOS 11 beta 5 launched in early August, but received very little coverage since.
Interestingly, at the time Redmond Pie reported that Touch ID could be used to authenticate pairing:
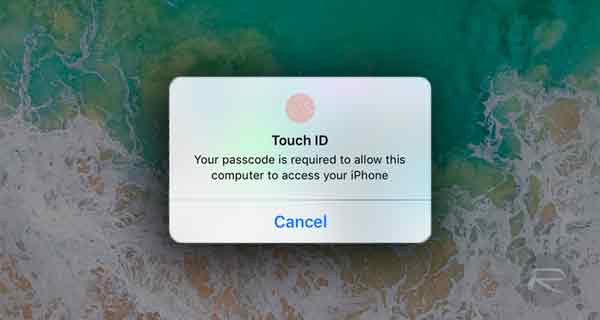
But in our tests with beta 7 and 8, iOS systematically asked for the passcode. We believe this change should be understood in the context of recent investigative overreach which have demonstrated how governments can (and will) force citizens to unlock their phones via Touch ID.
Requiring the passcode in this context is safer:
- In the U.S., passcodes are protected by the 5th Amendment.
- An unconscious victim cannot unwittingly give away his or her passcode.
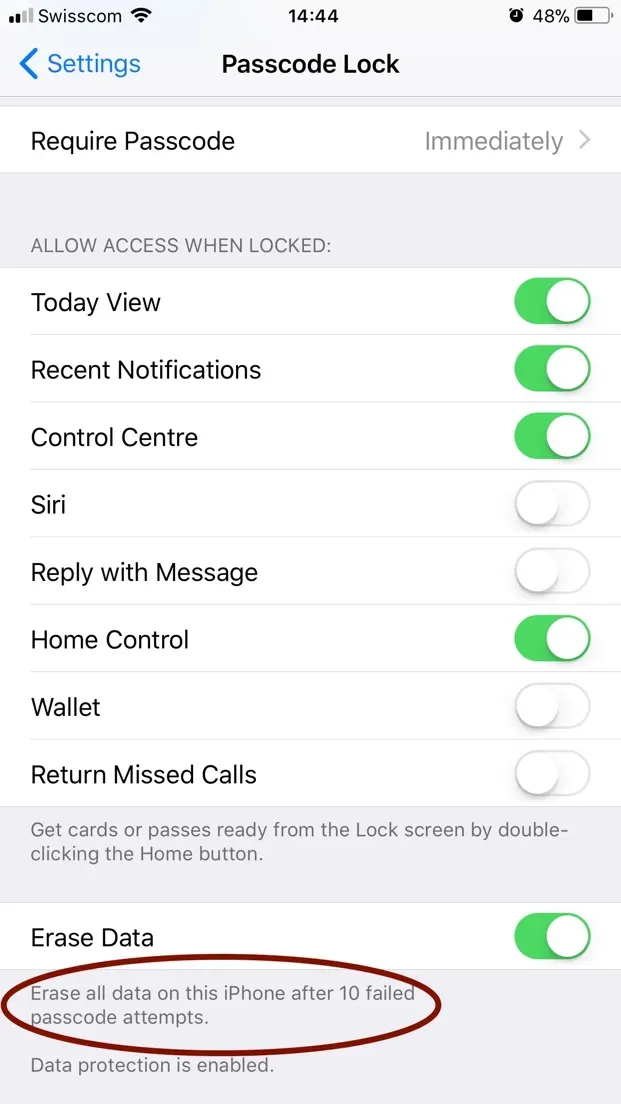
- Coercion can be easily resisted by entering a wrong passcode enough times to trigger a full wipe of the device, if the corresponding setting is enabled.
This hypothesis fits nicely with another similar iOS 11 security feature which temporarily disables Touch ID, providing as The Verge puts it a 'cop button'.
Why does this matter?
Apple doesn't make such moves randomly. iOS 11's increased pairing security was likely provoked by cases of identity theft, investigative overreach, and domestic or corporate spying.
To grasp how authentication protected pairing better safeguards user data in iOS 11, it is important to understand how iOS devices and computers interact. By default, a computer simply cannot access any data before trust is established between the computer and the device. This process is referred to as pairing.
In order to establish pairing:
- The iOS device must be connected to the computer via USB
- The iOS device must be unlocked
- The user must respond affirmatively to a Trust prompt on the iOS device
- The user must authenticate himself via the iOS device (since iOS 11 only)
Once pairing is established, the following data can be extracted directly, via USB or local Wi-Fi connection:
- Photos and videos, including location data
- Voice memos
- PDFs stored in iBooks
- User documents of productivity apps
A backup of the device can also be performed, granting access to even more personal information:
- ALL contents of the Messages app
- Chats from Whatsapp and other messaging apps
- Voicemail
- Call history
- Contacts
- Calendars
- Notes
- Safari browsing history and bookmarks
- Accounts (but not passwords)
- And more…
⚠️ Data can only be extracted from a backup if iTunes Backup Encryption has not been explicitly enabled by the owner of the device. At DigiDNA, we actively encourage all our users to enable backup encryption via clear prompts and warnings in our software.
Until iOS 11's new security features, pairing could be achieved without consent in the following scenarios:
- Device theft while device is unlocked (while gaming or reading emails for example)
- Temporary access by a family member, boss or colleague on false pretense ('Can I borrow your phone for a sec, I forgot mine and have an urgent call to make…')
- Coerced device unlock by law enforcement, border officials, etc…
Once pairing is effective, the attacker can access the victim's data via Wi-Fi whenever the attacker's computer is connected to the same Wi-Fi network as the victim's mobile device. This can happen without the victim's knowledge, the only sign being a sync indicator on the victim's phone if the attacker performs a backup of the target device. Accessing photos, videos, and user documents of some productivity apps' can happen completely silently.
Related to Face ID?
Apple's next flagship iPhone will most probably replace Touch ID with a face recognition authentication mechanism, Face ID. It is rumored to be very safe, integrating far more data points than Touch ID and being more immune to attacks than Samsung's similar efforts, thanks to the also much rumored 3D sensing capabilities of the new camera module.
But by nature, face recognition could make it even easier for law enforcement to coerce the public into unlocking their device: all it takes is to point the phone at it's owner. We don't yet know how Face ID will precisely work, but it could very well be that the fallbacks to good old passcode protected authentication we've evoked here are related.
How to protect yourself
Obviously, updating your iOS devices to iOS 11 when it will officially be released in September is a great first step.
Enabling backup encryption, even if you do not make local backups, is a good idea too. Backup encryption can be enabled with iTunes, or with iMazing (no license required).
If you think that your device may have been paired with a computer without your consent, you can break the pairing relationship by resetting location and privacy settings in your iPhone or iPad's Settings app: General > Reset > Reset Location & Privacy
Finally, don't share your passcode, and make sure that Erase Data is enabled in Settings > Passcode and Touch ID. Your data is yours only, keep it safe!