Device Management
Use Intune MDM with iOS devices registered in ABM/ASM for Automated Device Enrollment, in conjunction with iMazing Configurator for local provisioning

💡iMazing 3
This guide is for the legacy iMazing version 2. For information on version 3, please visit this page.
The purpose of this guide is to assist you in configuring Automated Device Enrollment in Intune MDM so that devices remain locally manageable with iMazing Configurator.
1. Create your supervising organization with iMazing Configurator
To begin, create your supervising identity in iMazing Configurator. This identity will be used in Intune for Automated Device Enrollment at step 2.
In the iMazing menu bar, under Configurator, choose Organizations:
Click on the '+' button located at the lower left corner:
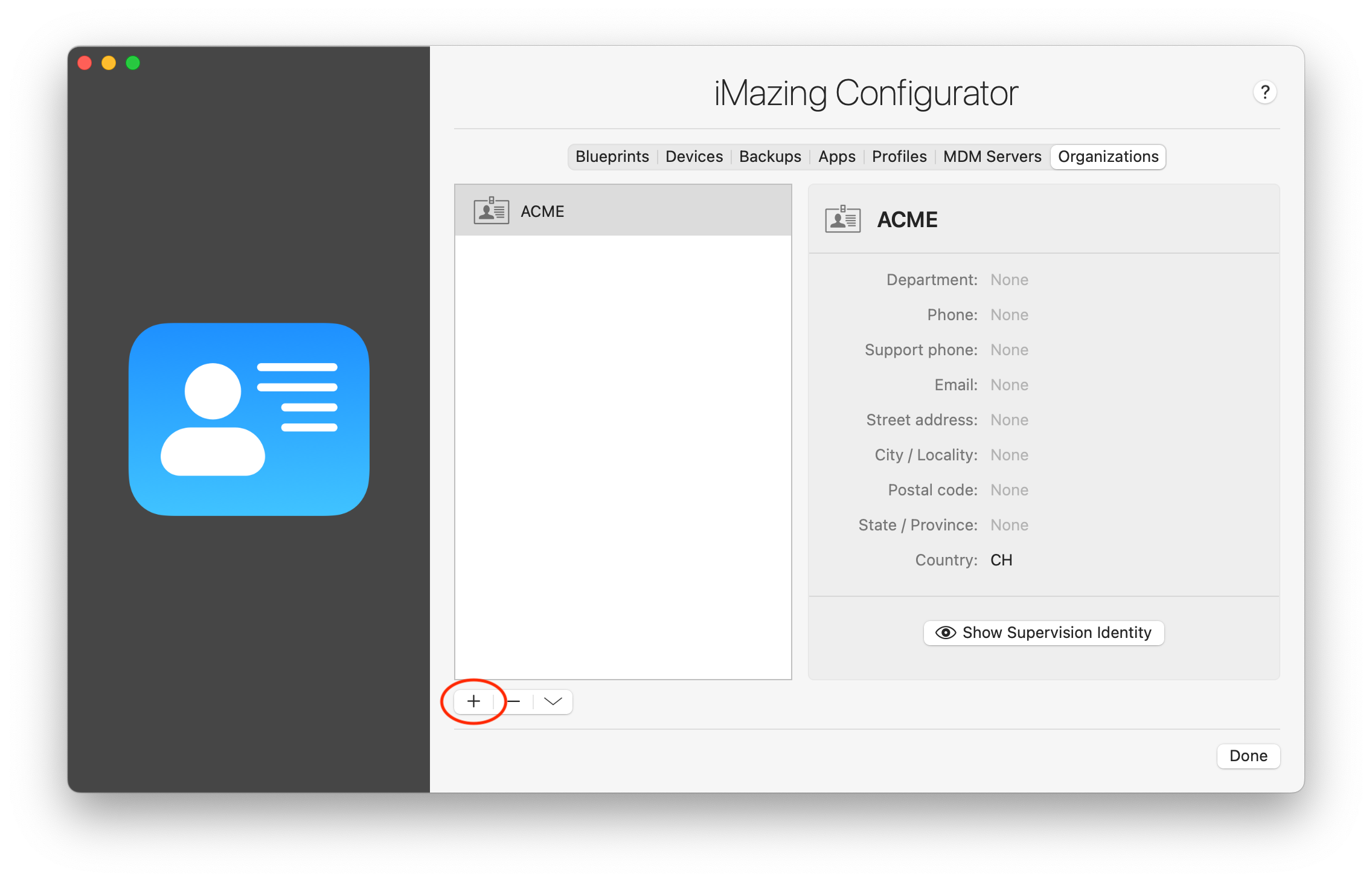
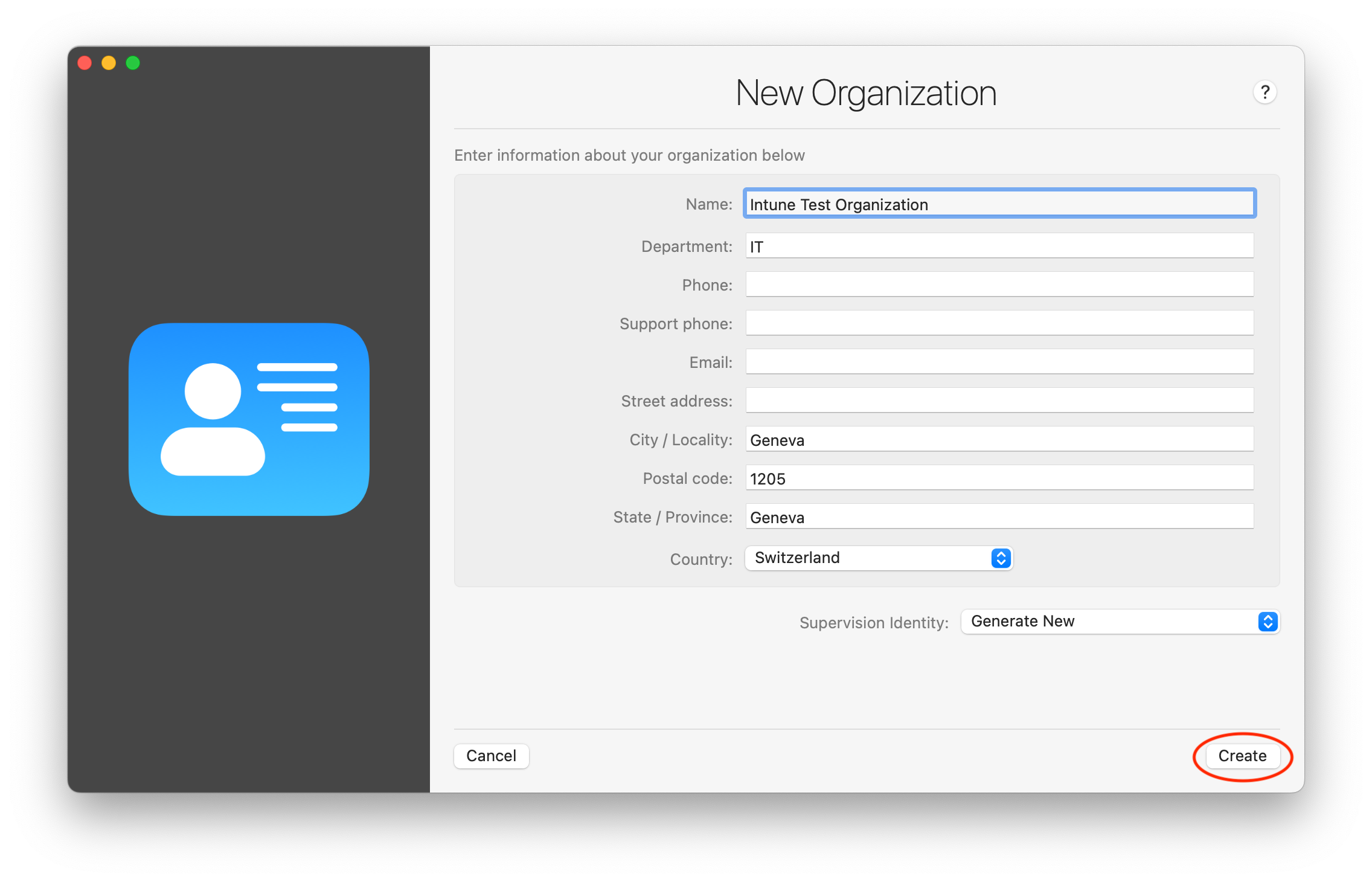
- In New Organization enter information about your organization. In Supervision Identity select Generate New and click Create:
- Enter your macOS user credentials and click Update Settings:
- Review your new organization and click Done:
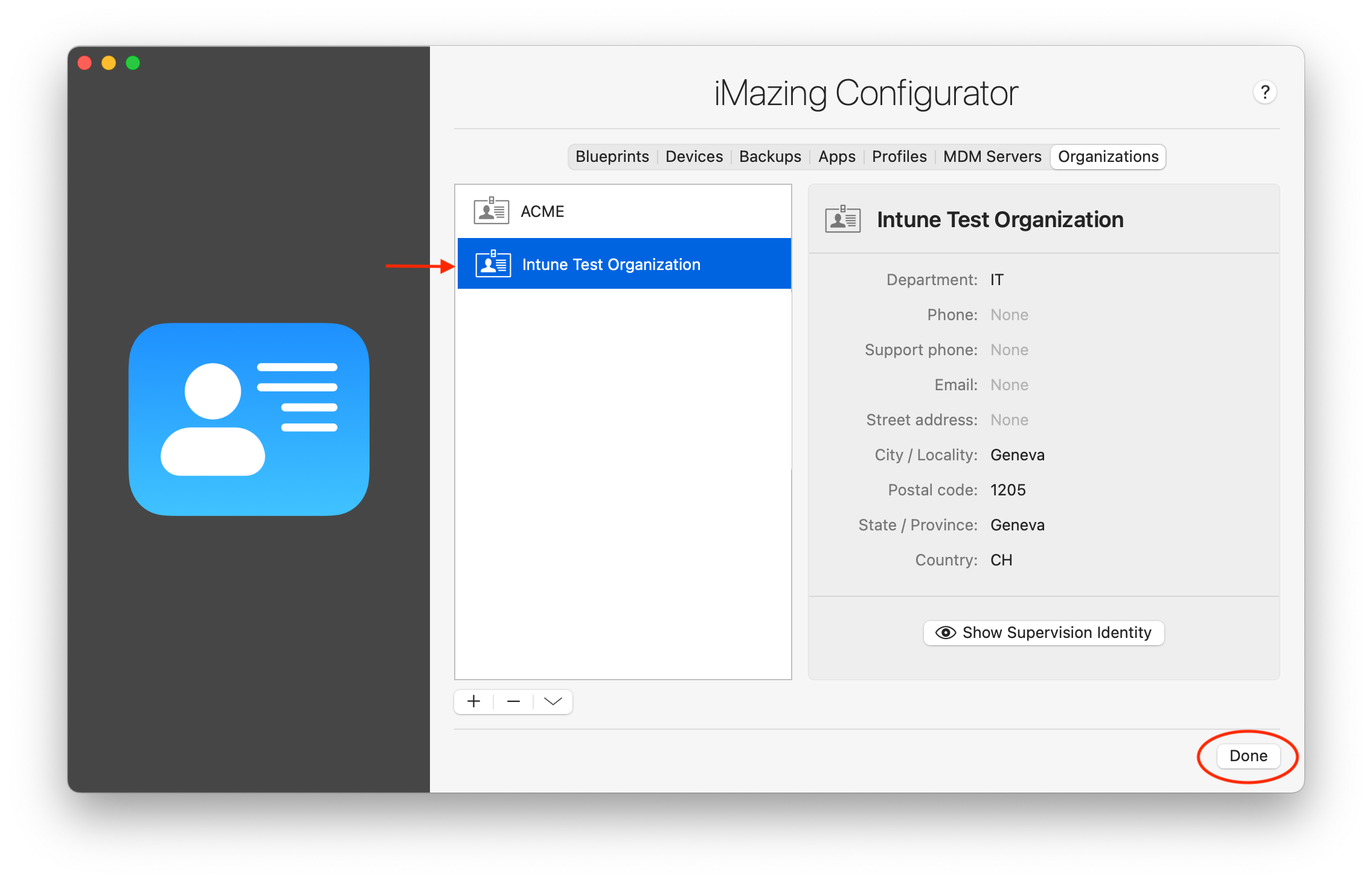
- Open the macOS Keychain app, select the login keychain, go to the My Certificates tab and with the search bar, look for your freshly created organization certificate (here we use Intune Test Organization). Select it and right-click to display the contextual menu:
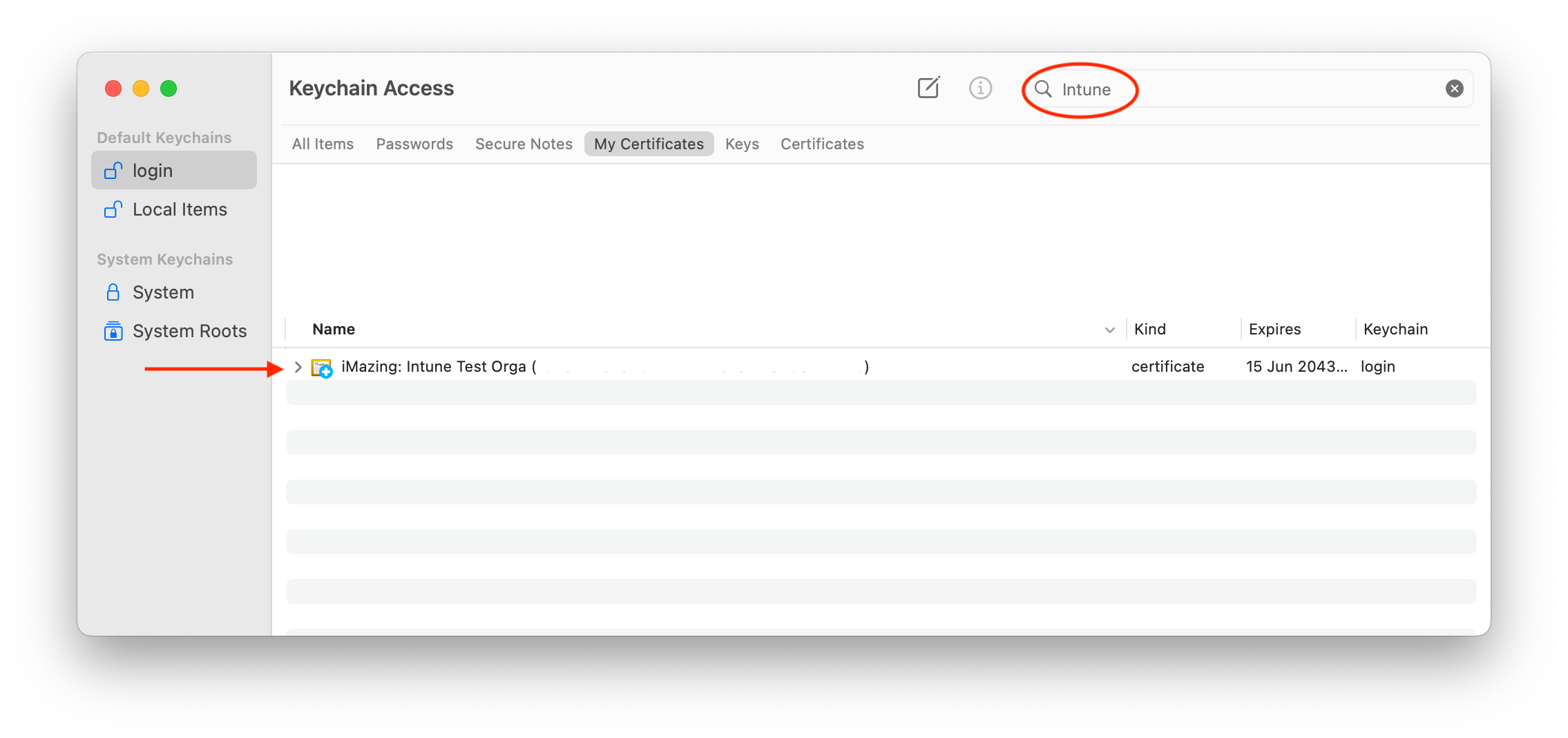
- Select Export "your organization certificate name":
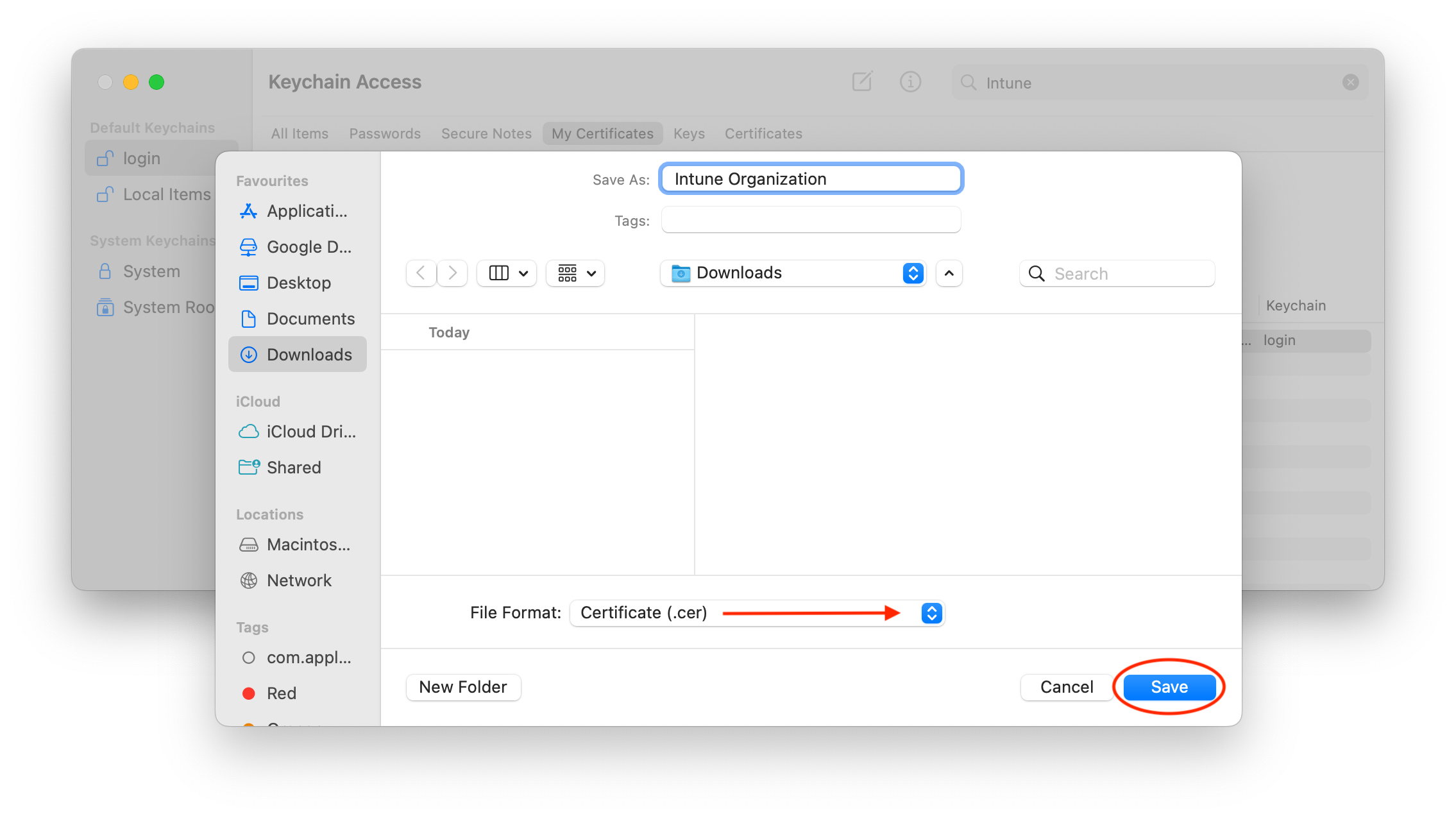
- Name your certificate and select .cer as file format. Once ready click Save:
2. Prepare your Intune MDM account for Automated Device Enrollment to work in conjunction with iMazing Configurator for local provisioning
Follow these steps to use the supervising certificate exported from iMazing Configurator in step 1 to create a new Intune Enrollment Program token.
The procedures may vary slightly depending on whether you use Automated Device Enrollment (ADE) or manually onboard your devices in Intune.
⚠ Important: Please note that several aspects of your overall Microsoft Azure tenant configuration may impact your migration. This guide will not cover the configuration of Azure. Additionally, we will not cover prerequisite steps, such as installing your Apple Push certificate.
- Log in to your Microsoft Intune console.
- Select Devices > Enroll Devices > Apple enrollment:
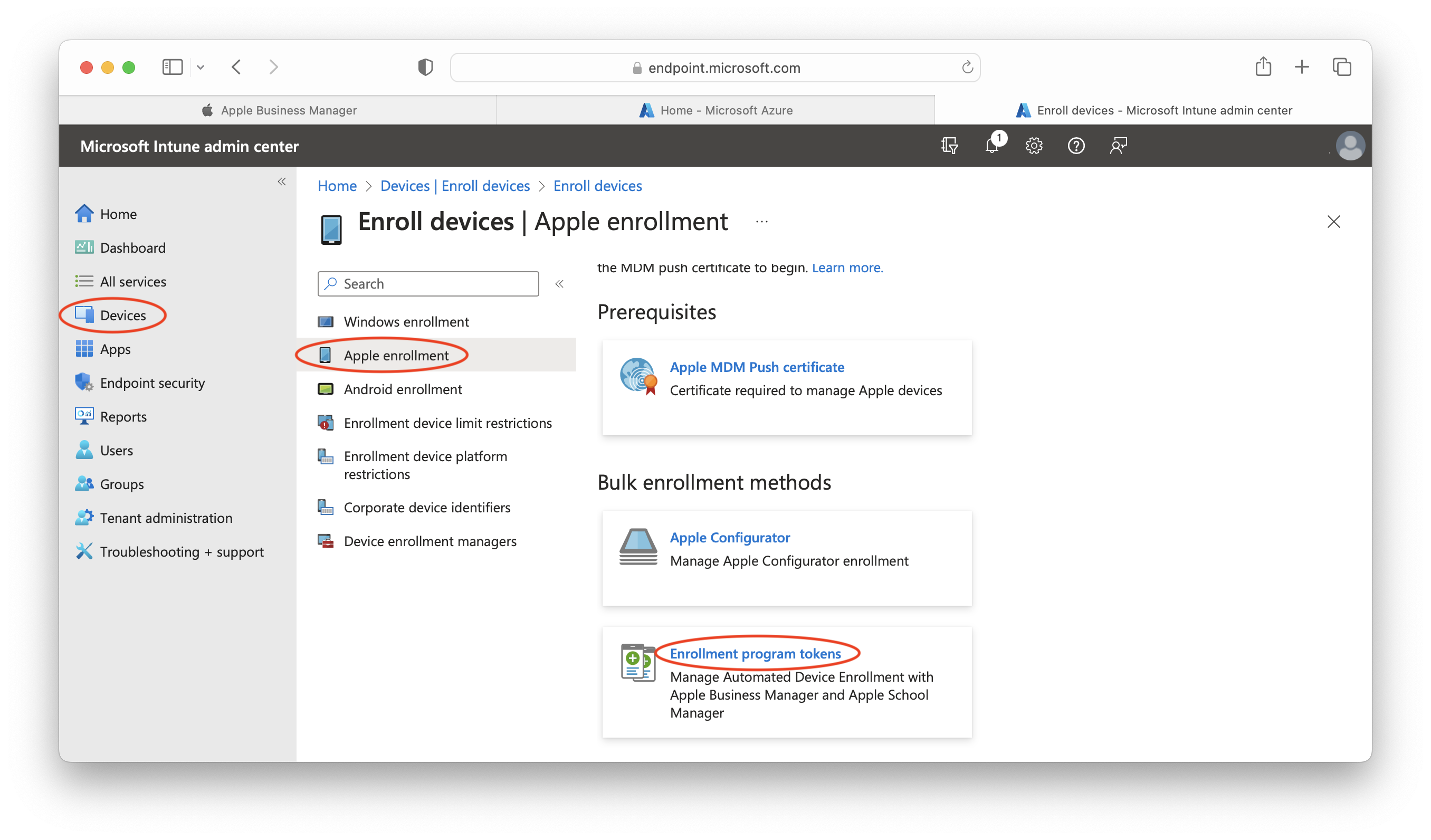
- Select Enrollment program tokens, choose your own and double-click on it:
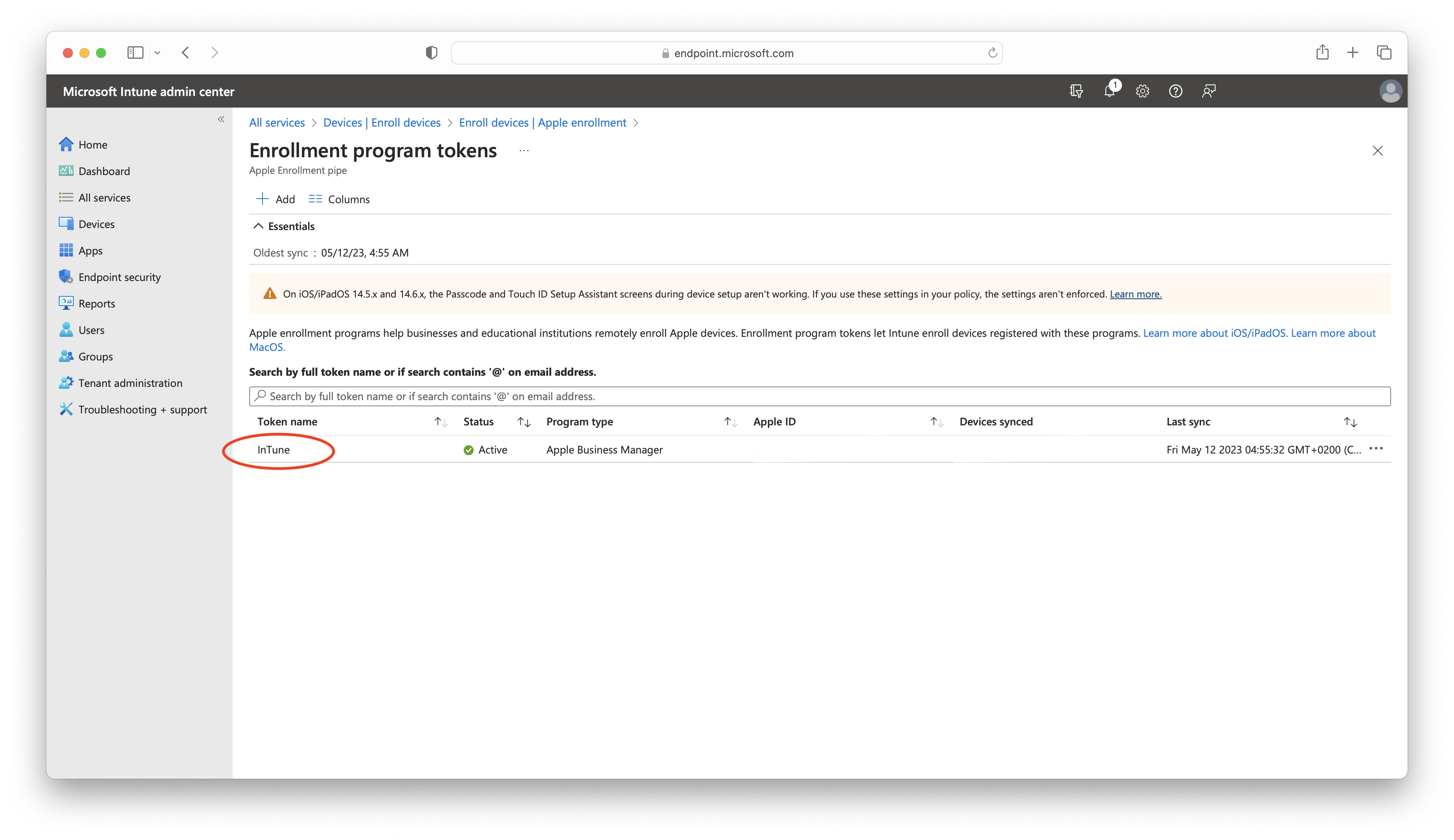
- Click on Profiles > Create a profile > iOS/iPadOS:
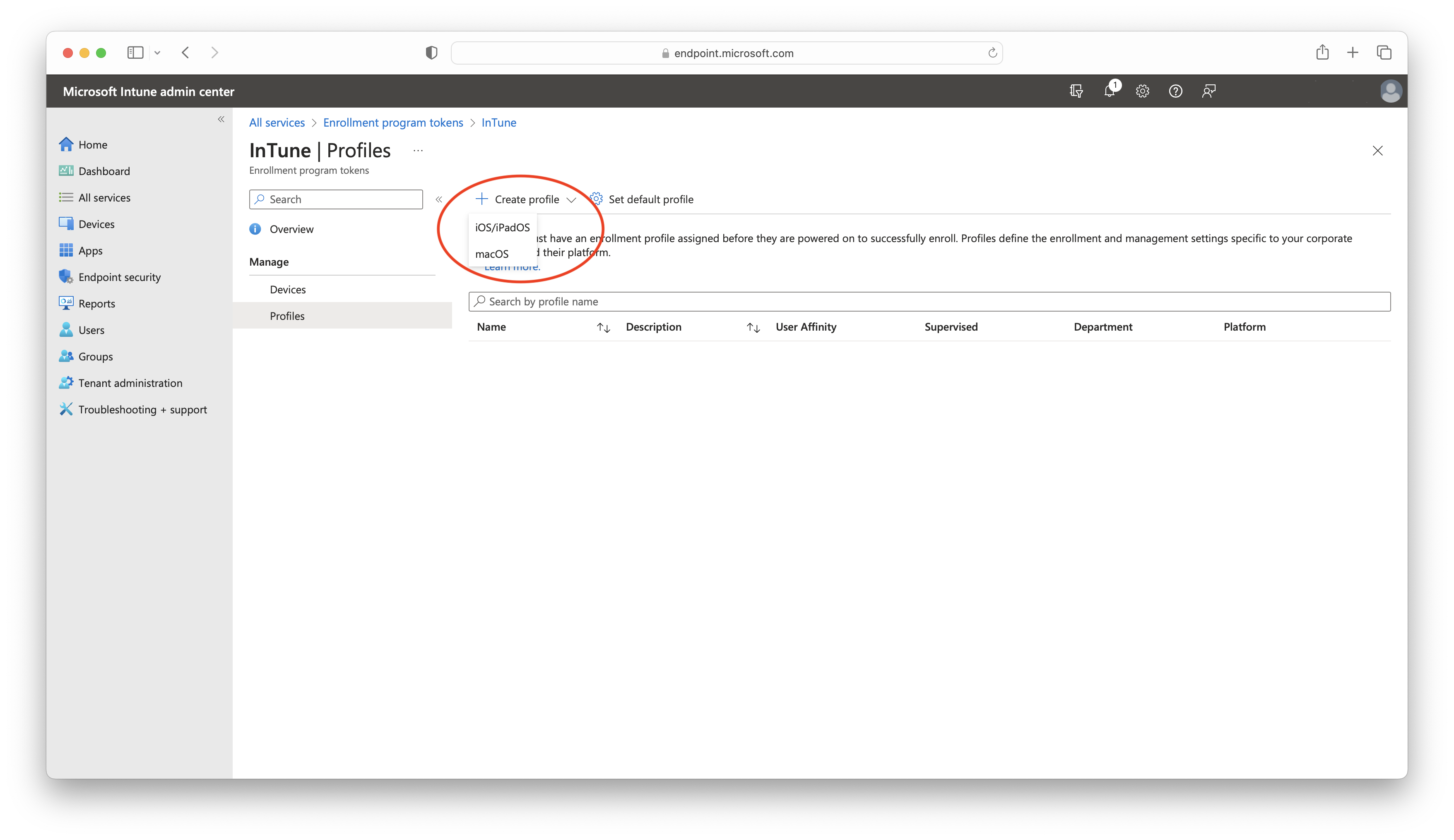
- Create a profile with a clear name, such as "ADE Enrollment," and add a description:
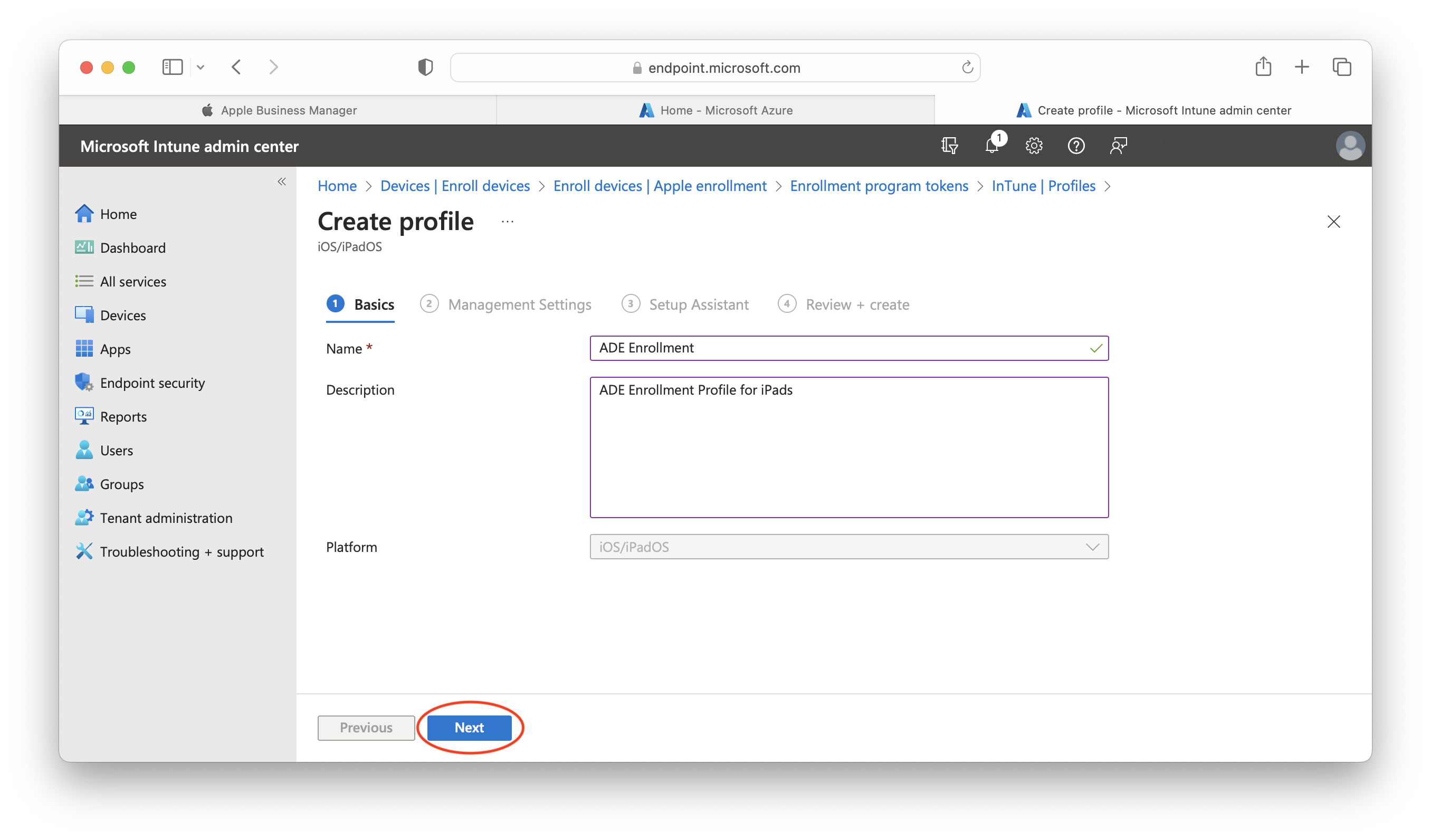
- In User affinity select Enroll without User Affinity (enrollment based on user accounts are not taken in consideration is this guide but are also supported):
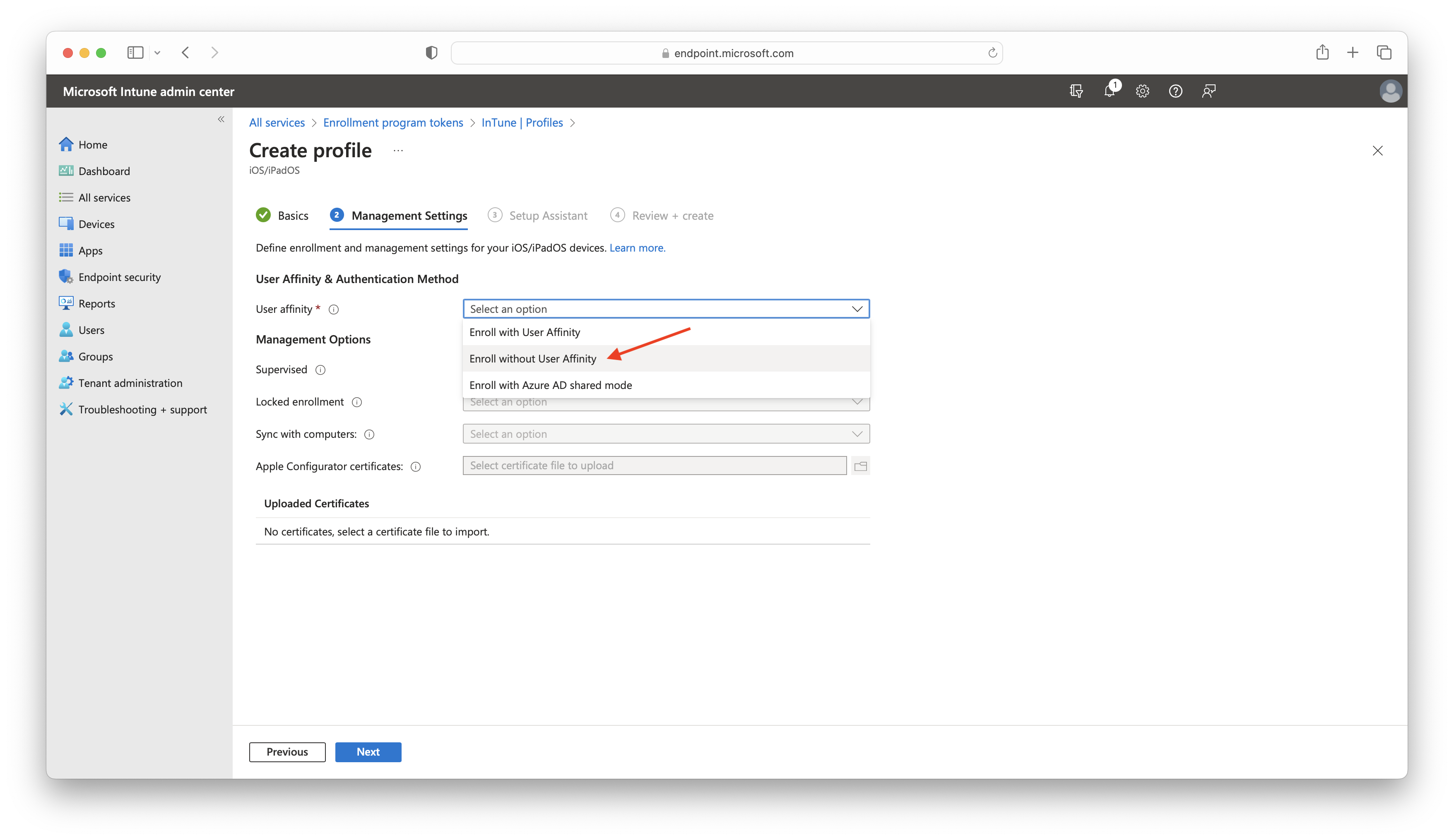
- In Supervise choose Yes.
- In Locked Enrollment, choose "Yes" if you do not want the end-user to be able to manually remove the management profile from the device's settings, otherwise select “No”.
- In a Shared iPad, select according to your needs.
- In Sync with computers select Allow Apple Configurator by certificate.
- In Apple Configurator certificates upload your Supervision certificate previously exported as .cer format (in our example Intune Test Organization).
- Select the other options according to your scenario and click on Next:
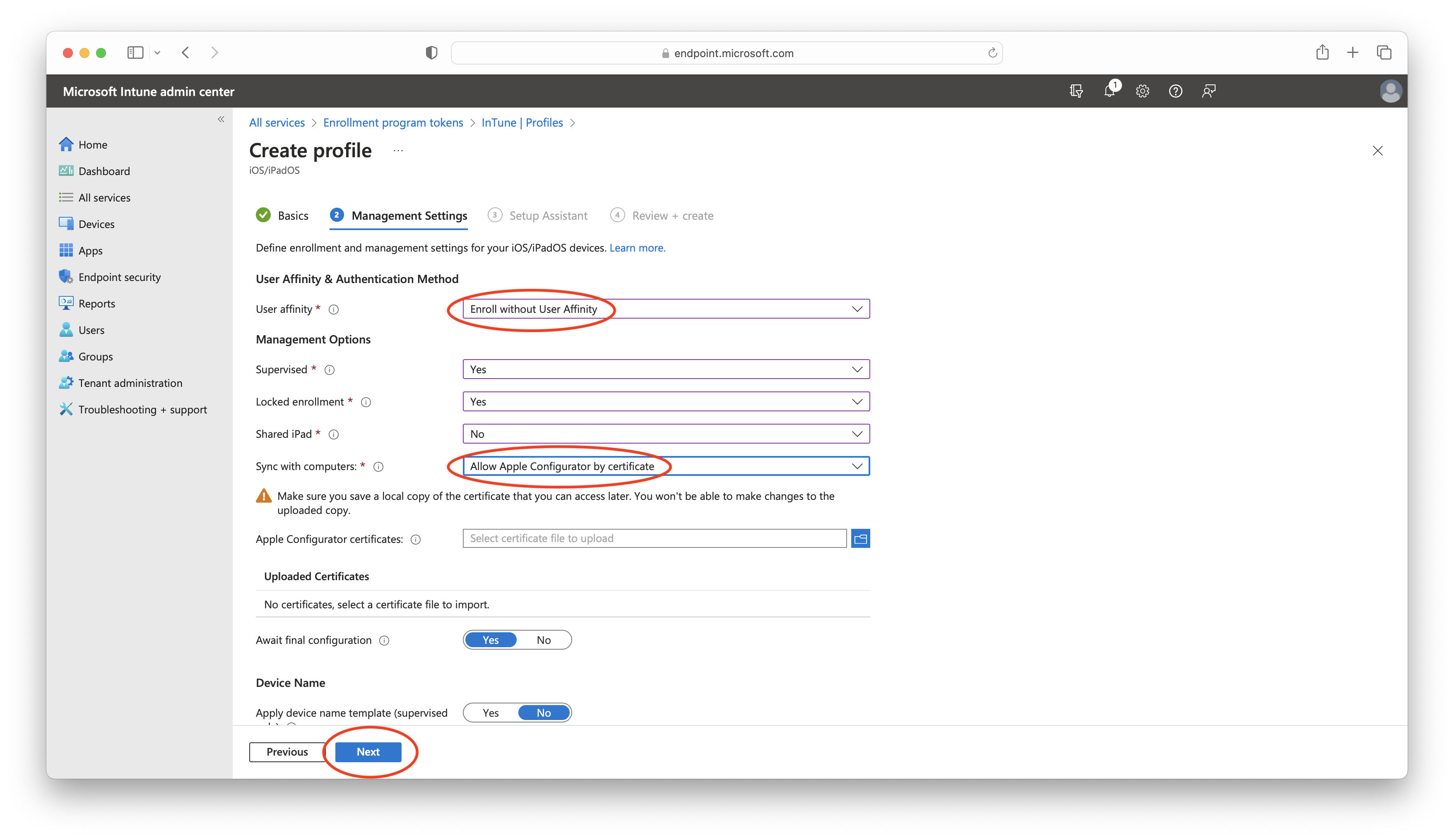
- In the Setup Assistant window, provide the requested information and choose the appropriate options for your scenario. Review your choices, and when you are ready to proceed, click on Create:
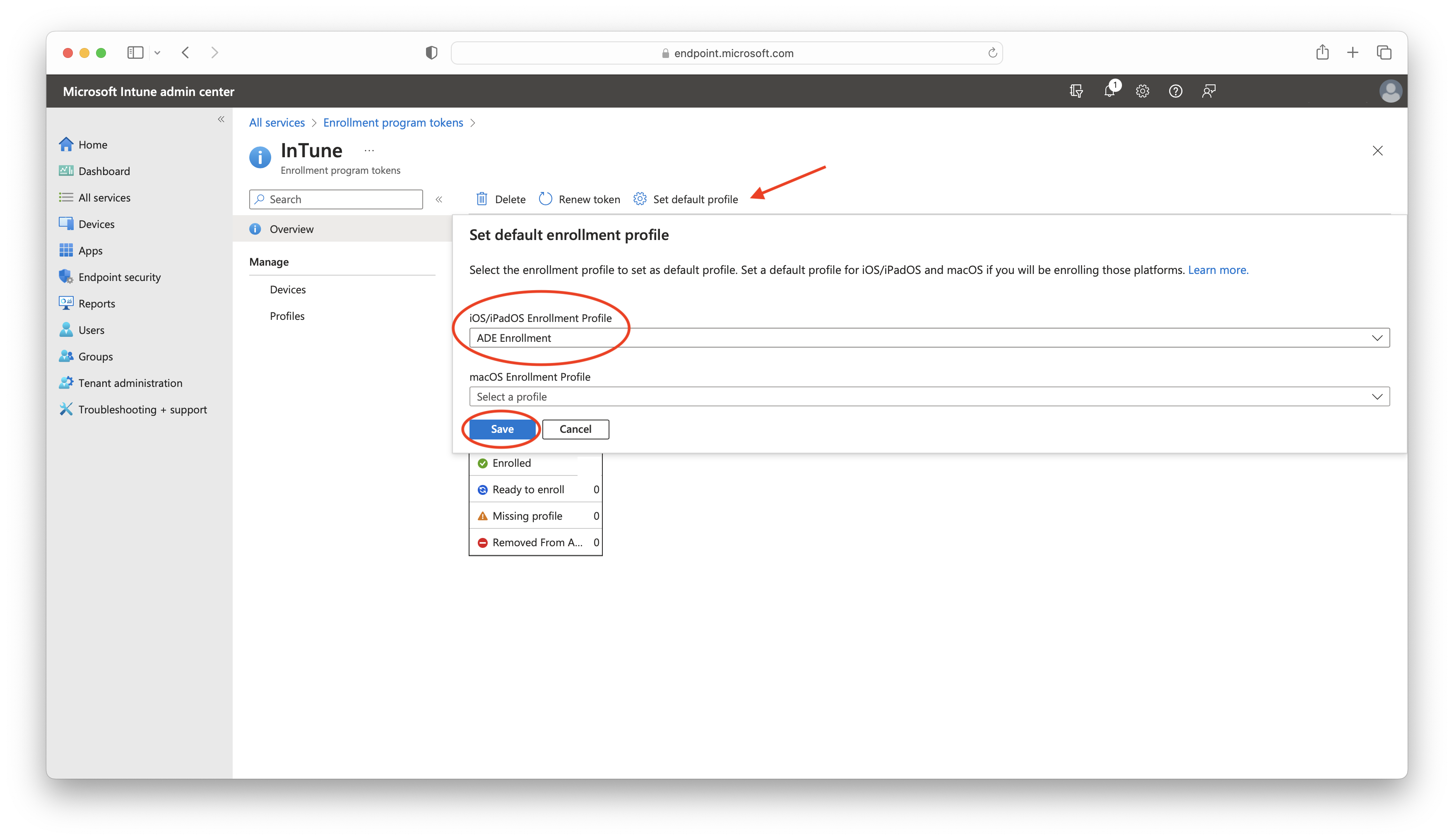
- To set your ADE Enrollment profile as the default profile, return to the Enrollment program tokens panel and click Set default profile. Then, select your ADE Enrollment profile in the iOS/iPadOS Enrollment Profile field and click Save:
- To enroll devices registered in ABM/ASM in Intune using ADE, first select the devices in the Devices section, then click Assign profile:
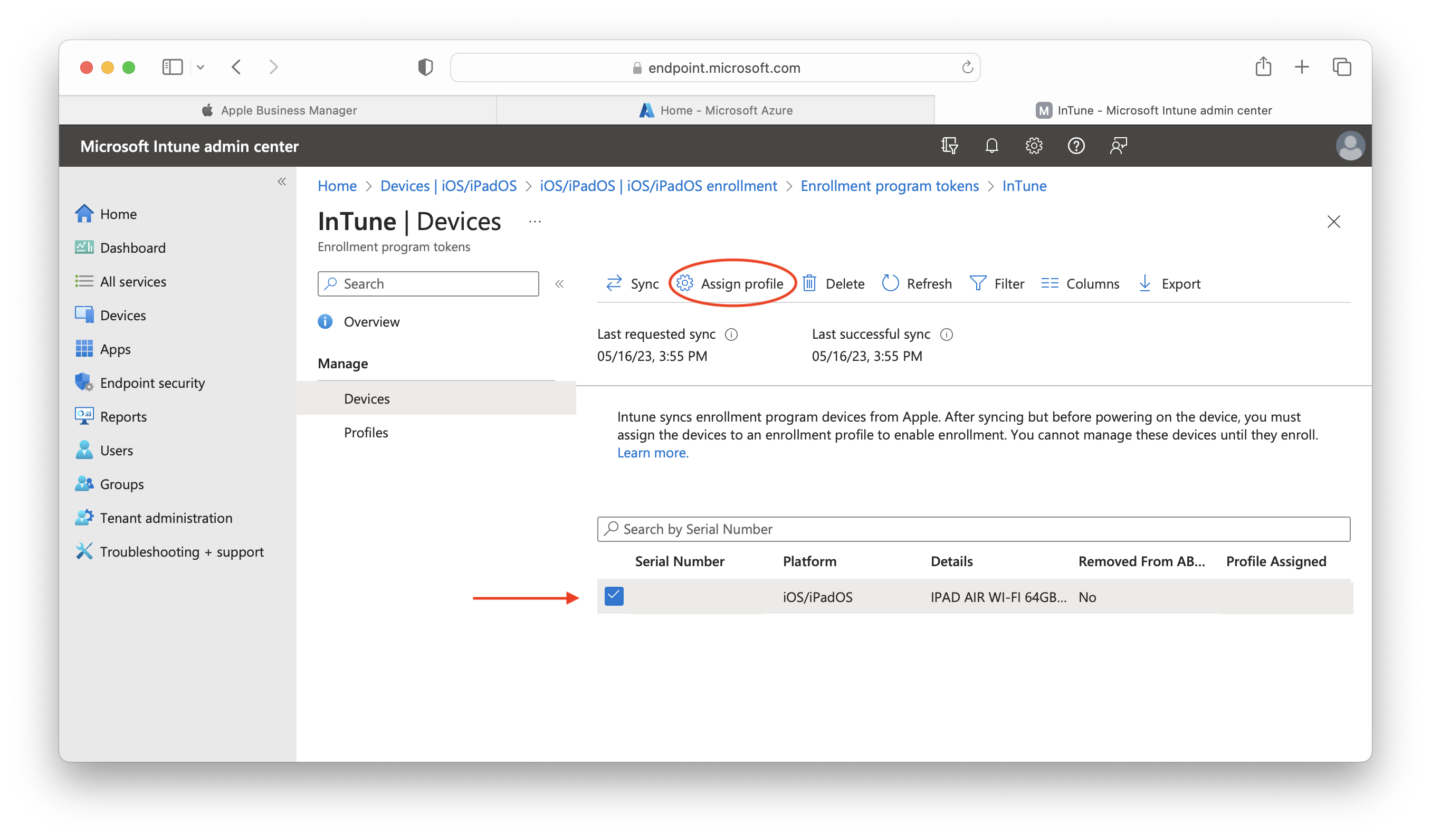
- Confirm your chosen Enrollment Profile and click Assign:
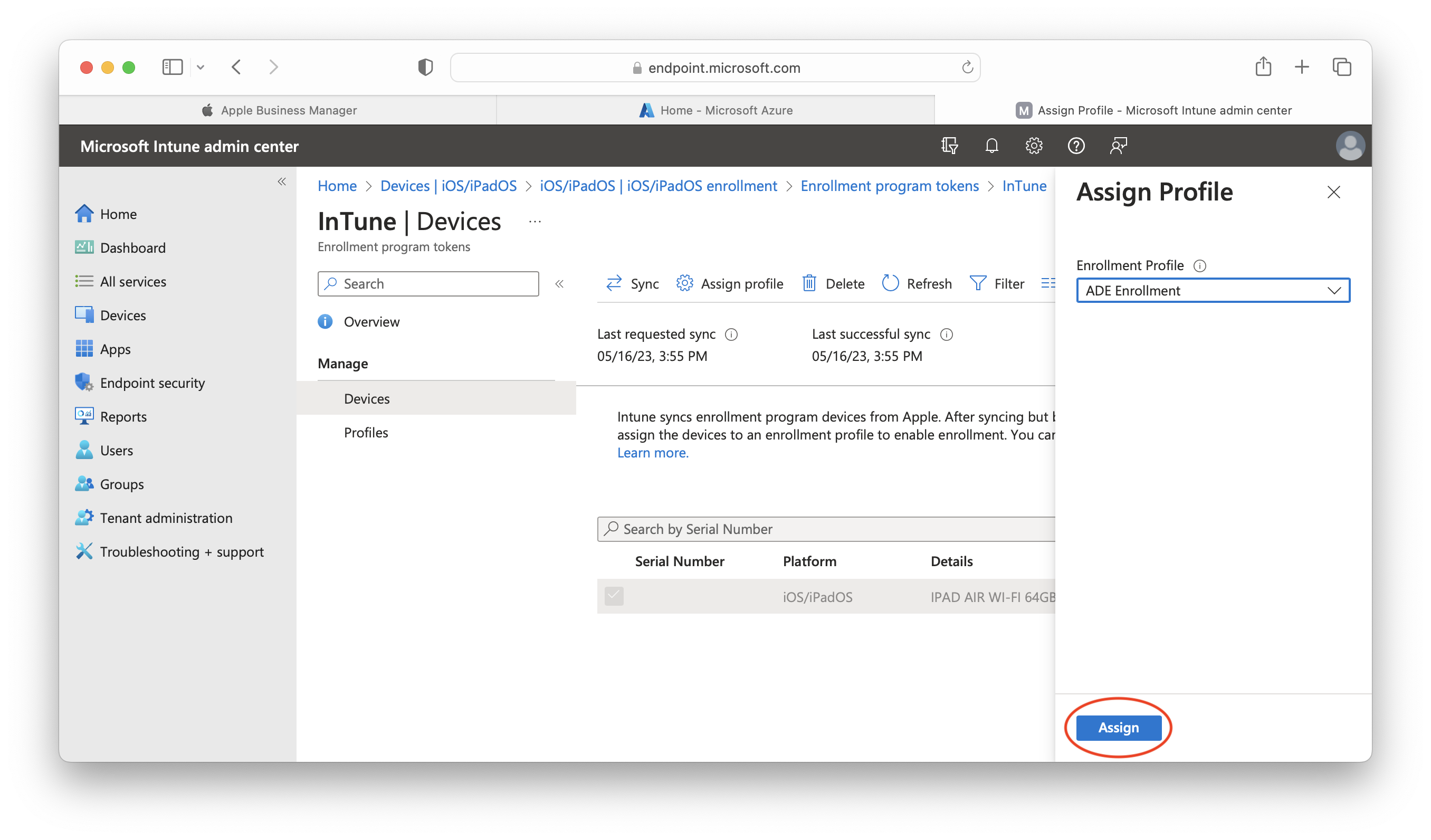
- To finish, click the Sync (ADE/DEP) button. As a result, the MDM server will communicate with Apple's servers to retrieve and update ADE/DEP-related information and configurations.
Once the device has been started and automatically enrolled, your local IT staff can interact with it using iMazing or iMazing Configurator. For example, they can back up sensitive local data for legal or compliance purposes, apply iMazing Configurator blueprints, and more.

